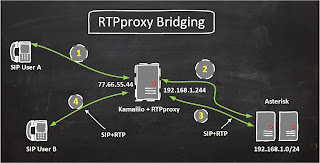
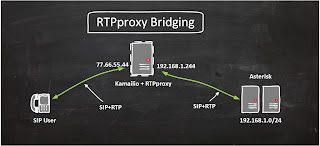
Time and again I see people getting stuck on RTPproxy integration with Kamailio. I recently got another opportunity to put RTPproxy in between the User Phones and Kamailio setup as depicted in the following diagram.
That is similar to what I've posted earlier on this topic. In this post I will try be more verbose and write each and every step I did to have RTPs flowing.
I assume you've a Kamailio installed and working and configurations file from Asipto Knowledge Base by Daniel and that there are TWO NICs configured with Public IP and Private IP as shown in the diagram above.
The important thing which I'm looking for from the configuration is the WITH_NAT tag. follow the code and see how the NAT is handled. route[NATMANAGE] is called at almost all important routes.
The overall idea is;
1- Install RTPproxy
2- Start RTPproxy in Bridged mode
3- Make Kamailio aware of multiple NICs
4- Add Private IP asterisks in dispatcher
5- Create a new route RTPPROXY to engage RTP-proxy whenever needed
6- Call in the RTPPROXY route in the NATMANAGE route.
7- Important Things to take care of.
So lets start following the steps.
Save and Exit
see that the DAEMON field points to the file in /usr/bin/rtpproxy
DAEMON=/usr/bin/rtpproxy
Lets copy the RTPproxy binary to that location.
Start up RTPproxy
Thats all.
Lets move on to step 3 involving Kamailio configurations.
We also need to put this line on the top definitions of kamailio.cfg file so kamailio use the NAT functions.
#!define WITH_NAT
Then declare the route:
Thats all for one day. Hope to have some comments and questions on this soon.
That is similar to what I've posted earlier on this topic. In this post I will try be more verbose and write each and every step I did to have RTPs flowing.
I assume you've a Kamailio installed and working and configurations file from Asipto Knowledge Base by Daniel and that there are TWO NICs configured with Public IP and Private IP as shown in the diagram above.
The important thing which I'm looking for from the configuration is the WITH_NAT tag. follow the code and see how the NAT is handled. route[NATMANAGE] is called at almost all important routes.
The overall idea is;
1- Install RTPproxy
2- Start RTPproxy in Bridged mode
3- Make Kamailio aware of multiple NICs
4- Add Private IP asterisks in dispatcher
5- Create a new route RTPPROXY to engage RTP-proxy whenever needed
6- Call in the RTPPROXY route in the NATMANAGE route.
7- Important Things to take care of.
So lets start following the steps.
1- Installing RTPproxy
root@Kamailio:~# cd /usr/src/ root@Kamailio:~# wget http://b2bua.org/chrome/site/rtpproxy-1.2.1.tar.gz root@Kamailio:~# tar zxvf rtpproxy-1.2.1.tar.gz root@Kamailio:~# cd rtpproxy-1.2.1/ root@Kamailio:~# ./configure root@Kamailio:~# make root@Kamailio:~# make install
Setup LSB script for RTP-proxyroot@Kamailio:~# cp debian/rtpproxy-default.ex /etc/default/rtpproxyedit the default file and put in the parameters.
root@Kamailio:~# vim /etc/default/rtpproxy
2- Start RTPproxy in Bridged mode
DAEMON_OPTS="-F -s udp:127.0.0.1:7722 -l 77.66.55.44/192.168.1.244 -d DBUG:LOG_LOCAL0 -u root"
Save and Exit
root@Kamailio:~# cp debian/rtpproxy.init /etc/init.d/rtpproxy root@Kamailio:~# chmod a+x /etc/init.d/rtpproxy
Open up the fileroot@Kamailio:~# vim /etc/init.d/rtpproxy
see that the DAEMON field points to the file in /usr/bin/rtpproxy
DAEMON=/usr/bin/rtpproxy
Lets copy the RTPproxy binary to that location.
root@Kamailio:~# cp rtpproxy /usr/bin/rtpproxy
Start up RTPproxy
root@Kamailio:~# /etc/init.d/rtpproxy start
verify that rtpproxy is running and listening on the specified 7722
root@Kamailio:~# netstat -pln | grep rtpp udp 0 0 127.0.0.1:7722 0.0.0.0:* 6554/rtpproxy
3- Making Kamailio aware of multiple NICs
Lets move on to step 3 involving Kamailio configurations.
root@Kamailio:~# vim /usr/local/etc/kamailio/kamailio.cfg
Insert the following line in global parameters section, just under where we define "listen=" or "port="
mhomed=1
That will ensure that Kamailio uses its Private IP to communicate with Asterisks on Private subnet. Don't forget this.
We also need to put this line on the top definitions of kamailio.cfg file so kamailio use the NAT functions.
#!define WITH_NAT
4- Adding Asterisks to dispatcher
Now Add Private IP asterisks in dispatcher: Follow my post on adding dispatcher to the plain configurations from here: http://saevolgo.blogspot.com/2011/11/how-to-increasing-voip-services.html
5- Writing some Kamailio routing logic for RTPPROXY
That was easy, now the real thing the addition of RTPPROXY route which I modified a little bit from the last link mentioned.
To have the code working I have used the SQLOPS module configured to query kamailio.dispatcher table as the AVPOPS module was already busy.
NOTE: Using the DB query is a costly operation BUT it allows me to detect if Kamailio is sending call to Dispatcher listed IPs or not. I have a mix of Asterisks on Private Subnet and on Public Subnet and if the Asterisk dispatcher has chosen or the call is coming from is a Private IP then engage RTPproxy. This detection is handled by IPOPS module and its function is_ip_rfc1918()
NOTE: Using the DB query is a costly operation BUT it allows me to detect if Kamailio is sending call to Dispatcher listed IPs or not. I have a mix of Asterisks on Private Subnet and on Public Subnet and if the Asterisk dispatcher has chosen or the call is coming from is a Private IP then engage RTPproxy. This detection is handled by IPOPS module and its function is_ip_rfc1918()
loadmodule "ipops.so"
loadmodule "sqlops.so" modparam("sqlops","sqlcon","ca=>mysql://openser:openserrw@localhost/kamailio")
Then declare the route:
# RTPProxy control route[RTPPROXY] { if (is_method("INVITE")){ sql_query("ca", "select destination from dispatcher where destination like '%$dd%'","ra"); if($dbr(ra=>rows)>0){ $avp(duip)=$(du{s.select,-2,:}); if (is_ip_rfc1918("$avp(duip)")) { xlog("L_INFO", "Call is going to private IPv4 Media Server Engage RTPProxy Now\n"); #rtpproxy_manage("crwie","192.168.1.244"); rtpproxy_manage("rwie"); } } else if(ds_is_from_list()){ if (is_ip_rfc1918("$si")) { xlog("L_INFO", " Call is coming from a private IPv4 Media Server Engage RTPProxy Now\n"); #rtpproxy_manage("crwei","77.66.55.44"); rtpproxy_manage("rwei"); } }else if(!ds_is_from_list()){rtpproxy_manage("rwie"); } }}
6- Using RTPPROXY route
Add the RTPPROXY route just where the FLT_NATS and FLB_NATB flags are tested.if (!(isflagset(FLT_NATS) || isbflagset(FLB_NATB))){ return; }route(RTPPROXY);
Now Save and Exit the kamailio.cfg file.
Restart Kamailio.
root@Kamailio:~# /etc/init.d/kamailio stop
root@Kamailio:~# /etc/init.d/kamailio start
7- Helpful Things to know
Asterisk needs to have the peer declared for kamailio using its Private IP.
[Kamailio]
type=friend
host=192.168.1.244
port=5060
disallow=all
allow=gsm
allow=g729
allow=alaw
allow=ulaw
context=SBC-Incoming
canreinvite=no
insecure=port,invite
nat=force_rport,comedia
qualify=yes
directrtpsetup=no
See that I've used "directrtpsetup=no" so that Asterisk don't decide to go direct with the End caller.
Use xlog lines in kamailio.cfg file to follow the call.
The way I always setup my whole environment is that Kamailio handles the REGISTRATIONs and only INVITES are load-balanced to Asterisks or FreeSWITCHes where they receive the call from Kamailio peer and execute dialplan applications and IF call needs to dial out they dial the destination back to kamailio.
Kamailio needs to detect the call coming FROM the Media-Servers (ds_is_from_list() function)
So I know when a user calls in and when the call comes in from the media-servers.
Always try to first have an echo test working for calls. I use Asterisk application Echo() and when I dial in from user I get my own audio echoed back and I know that atleast my audio path is complete. This never tells you that your setup is 100% perfect but it is a good way to know if you're headed right direction.
Wireshark is a great Friend. Use it to examine everything in depth. No matter what I do I always need Wireshark to visually see what is going on with the SIP packets, that gives me everything I need to know to make things right.
Always try to first have an echo test working for calls. I use Asterisk application Echo() and when I dial in from user I get my own audio echoed back and I know that atleast my audio path is complete. This never tells you that your setup is 100% perfect but it is a good way to know if you're headed right direction.
Wireshark is a great Friend. Use it to examine everything in depth. No matter what I do I always need Wireshark to visually see what is going on with the SIP packets, that gives me everything I need to know to make things right.
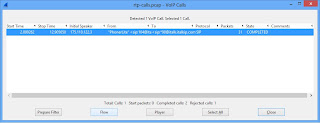
root@Kamailio200:~# tcpdump -i any -s 0 -w rtp-calls.pcap -vvv tcpdump: listening on any, link-type LINUX_SLL (Linux cooked), capture size 65535 bytes 1666 packets capturedDownload this "rtp-calls.pcap" file and open it up in Wireshark. Click "Telephony" from the menu bar and select "VoIP Calls"
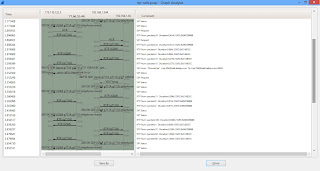
Hit the Flow button and you'll see beautiful arrows showing the direction of SIP and RTP packets.
On the very Left Hand side is my Soft Phone's Public IP address, then 77.66.55.44 is kamailio's WAN side, and suddenly we see 192.168.1.244 which is Private IP of Kamailio communicating with an Asterisk on 192.168.1.36
The Bold arrows labeled RTP are flowing in both direction means all Perfect.
Thats all for one day. Hope to have some comments and questions on this soon.